
Smart contracts of blockchain-based applications can appear quite complex but the simplest fact to be understood is the importance of the smart contract security audit. As important as they are in ensuring the smooth functioning of the business’s applications, the protection of smart contracts themselves is left untethered. In today’s times, security is a crucial component for any business as its absence can create high costs in revenue and reputation as a result of attacks.
Given the irreversibility and immutability of transactions with blockchain-based applications, smart contract implementation and security can arise as a problem. You may compromise the entire contract and associated assets because of the late discovery of security vulnerabilities in smart contracts.
The Relevance of Smart Contract Security Audits
As we covered before, both the role of smart contracts and their security implementation are important. Smart contract security audits assist in the early detection and resolution of vulnerabilities without letting them turn into a security issue later. They ensure that the code is optimized with no misconfigurations for better performance of the smart contracts. Website security audits also ensure the protection of third-party providers and endpoints of transactions such as wallets from specialized and general attacks.
What Kind of Attacks Can You Expect Against Smart Contracts?
Ensuring adequate security barriers for smart contracts protects them from replay, short address, reentrancy, overflow and underflows, and reordering attacks. This makes smart contract security audits important for firms that own and operate decentralized applications as a part of their core operations. Smart contract developers also benefit from the process when designing them for ICO startups who, in turn, use these methods to garner the trust of their stakeholders and clients.
3 Steps for Smart Contract Security Audits
Let’s briefly go through some of the main steps involved in smart contract security audits to gain a general idea of its functioning:
Specification of smart contracts
An outsider testing your application’s smart contract should be able to understand the overall infrastructure and purpose. Therefore, the first step in a smart contract security audit should be to hand over relevant documentation detailing the architecture of the smart contract and its intended purpose.
Once the hacking team gets an idea of the design and thought process behind the smart contract, they’re able to design their testing approaches accordingly. Here, the ‘code freeze’ step, or the stage of code finalization, is important for the testers as this is where their responsibility of finding and rectifying vulnerabilities ends. Auditors and code developers come to a consensus regarding the final commit hash before the security audit.Testing
Since there are different steps involved under the smart contract depending on its features, vulnerability detection can go any way. For example, unit tests go for debugging in individual functions and integration tests cover larger portions of code. Always remember to define the scope of the smart contract security audit as improved testing coverage could eliminate a larger number of vulnerabilities. It also helps testers to understand the proper functioning of the smart contract and gain informal insights into its possible errors on a larger scale.
For this, running a test suite would be a better option – if the code passes a large number of tests, you’ll know that there are a lesser number of easily detectable vulnerabilities. On the other hand, a higher number of failed tests would call for a proper security audit and the need for serious modifications to address vulnerabilities.When talking about testing processes, it’s important to address the proportion of automated and manual testing techniques. Automated tools will help you in discovering the general vulnerabilities and streamline the audit process but manual testing will help provide the context from the smart contract developers’ mindsets. Therefore, implementing both will result in an efficient smart contract security audit.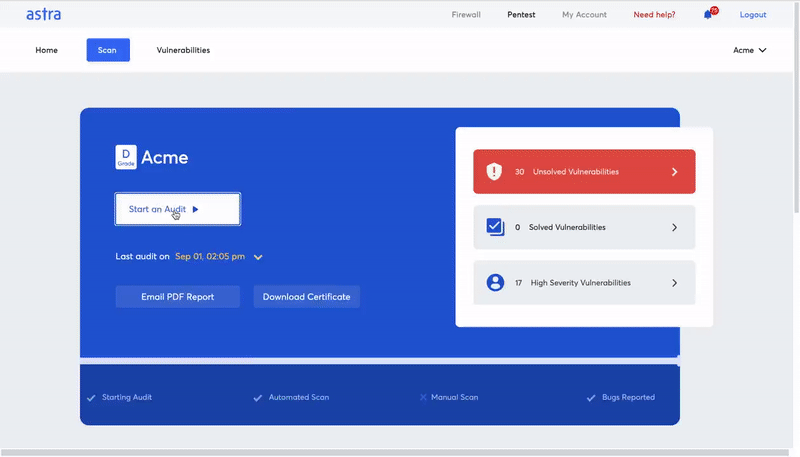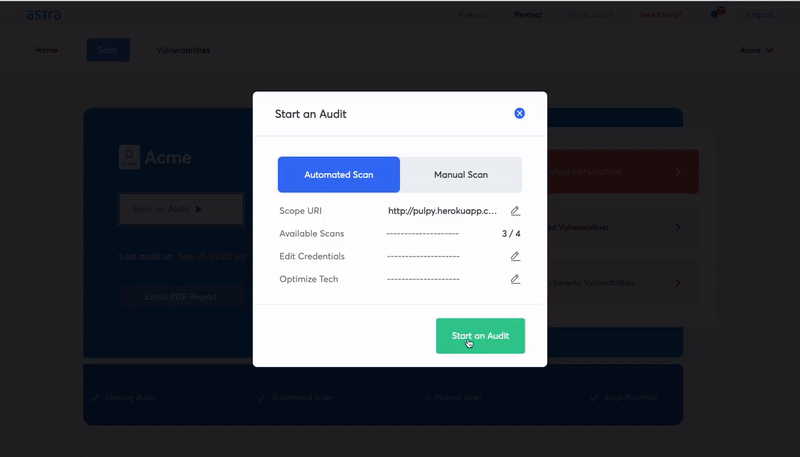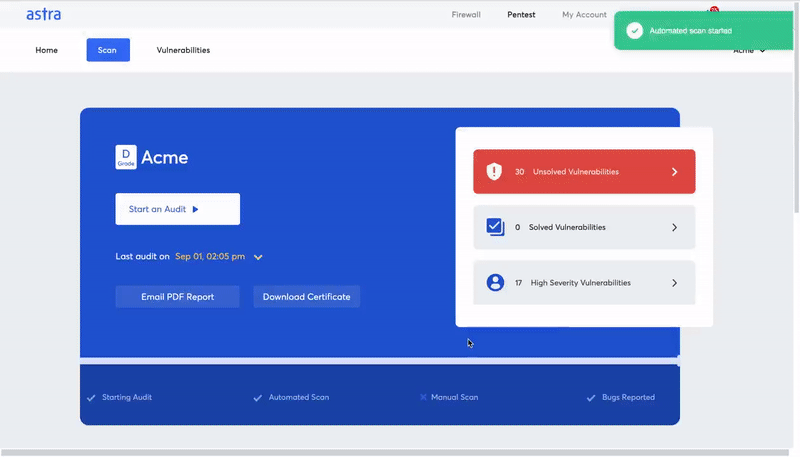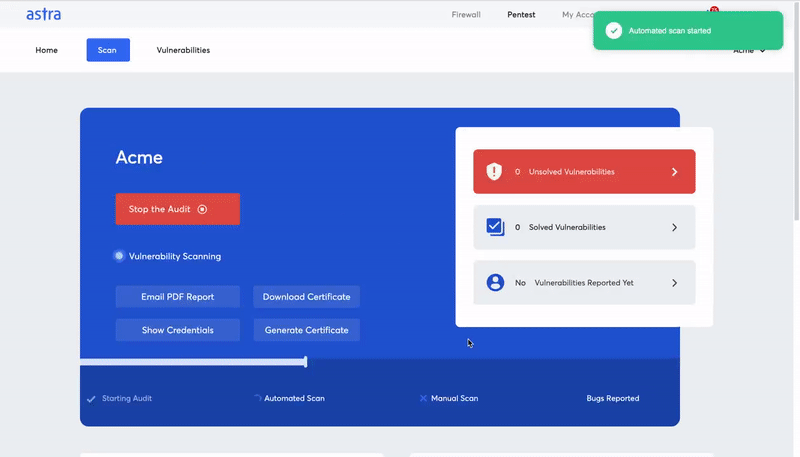
Image Source: Astra Pentest Dashboard
Pay attention to the line coverage mentioned by your third-party service provider as a greater portion of code being tested would indicate lesser vulnerabilities. Anywhere upwards from 85-90% of line coverage indicates a good testing scope.Preparing the audit report
As with all penetration testing procedures, the final audit report should cover detailed reporting and analysis of the test results, including the testing approaches taken. Teams in charge of the testing and designing of the smart contract should come together and analyse the findings and their business implications before looking into remediation procedures for vulnerabilities. This will help in better implementation of the final recommendations as a solution to the problems identified and other steps to be taken in the future.
These are a few of the generalized steps involved in a smart contract security audit. However, in today’s scenario, where specialization is the heart of every firm, unique situations may demand different testing approaches to fully understand the security situation of each firm and its products and services.