The Internet has always been our best buddy in terms of almost everything. As a layman, we can say that the internet is a ‘blessing’. But it can also be harmful. Yes, the internet is an enigma, especially for those who can be easily tricked and robbed due to their minor or zero knowledge about cyberspace.
Internet data has 3 different levels:
- Clear web/Surface web
- Deep web
- Dark web
The clear web is a general search engine that we see in our daily life, but the unclear and blur picture of the latter needs an explanation. Let’s understand the difference between the deep web and the dark web.
Deep Web
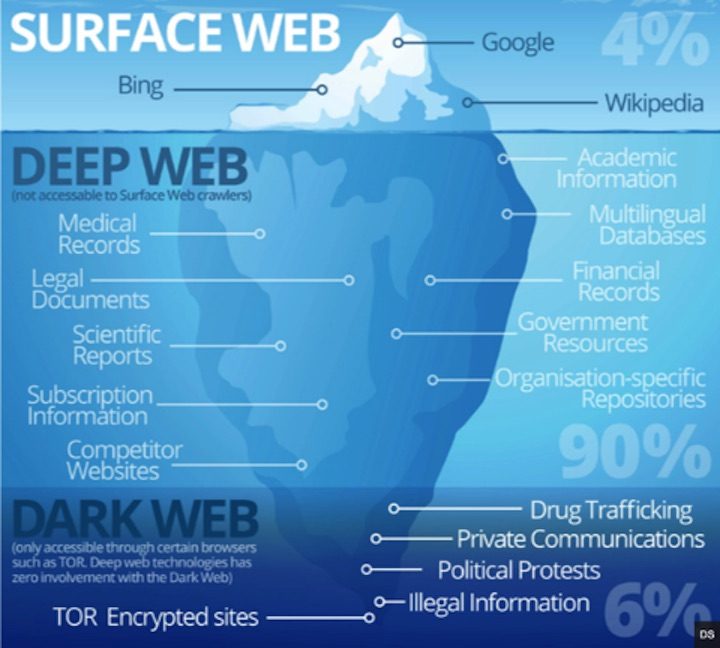
Some search queries cannot be accessed through standard search engines like Google or any social media. These are the secured bits of information that require special credentials and are encrypted with high security. They can be inferences, medical, scientific, and business databases or archived pages from any governmental authority. Such documents cannot be accessed without the permission of an authorized entity.
It is important to know that the actual amount of data on the internet is a deep web and it is approximately 90%. The deep web is ethically neutral, it can be used for good as well as bad purposes. In contrast, the dark web is hidden due to its links for shady business and cybercrime.
It should be considered that deep web is not a dark web but all dark webs are a part of the deep web. Precautions and prior knowledge are suggested before operating these sites. (refer the text below)
Dark Web
Unlike the deep web, all the information on the dark web is often not meant to be publicly accessible. However, you cannot access the special software without the encrypted credentials which are anonymous or fake so that the identity of the account holder cannot be detected. There are numerous systems that can make this software, naming “The Onion Router” or “TOR”.
TOR was invented by the American Navy to protect important military information and other security information but it was overtaken by some online mafia systems that used it for nefarious activities. Due to its high anonymity, it was used for human trafficking, drug, and weapon dealings.
This software is designed to produce node connections worldwide and uses large networks. Each node is meant to decrypt only the amount of data that tells ‘Where to bounce next?’ These successive peeling back layers inspire the name of The Onion Router (TOR).
Although the dark web also has some nobler uses like, it can protect human/social rights activists, or protecting data from surveillance, people with fringe political views, etc.
Mindlessly, this information will be regarded as of no use if you do not possess any curiosity to visit the dark web! Metaphorically, you do not hold any desire to snoop around the secret chambers. But if you do, read the word of caution.

DANGER!
It is not advised to access the dark web from your browser with the real or fake credentials because it has a 100% chance that you can face fraud and your credential can be hacked causing a great loss of your data.
But if you have to visit the dark web, out of curiosity or some work. Some advised precaution is listed below:
- Avoid browsing the dark web.
- Use a secure browser like Tor.
- Be prepared and get the domain knowledge before stepping in those areas.
- Use fake credentials and a strong password that cannot be hacked.
- Ensure anti-malware protection for your computer.
- Do not install or click on any pop-up notification for subscription.
Here are some brief points of differences between the two webs are given below for your quick reference.
| Deep Web | Dark Web |
|---|---|
| Not indexed for public use. | Indexed for public use. |
| Standard search engines cannot access this easily. | The common search engine may access. |
| Legal data is stored with high security. | Illegal data is stored with no security. |
| An encrypted credential is needed to operate. | The decrypted anonymous credential can be used. |
| Mostly used by banks and government authorities for data keeping and private companies/individuals may also use it. | Mostly used for cybercrime such as drug dealing, human trafficking and illegal hacking for online robber etc. |
| Legal niche. | Illegal niche. |
| A huge part of the internet. | A smaller part of internet. |
| Safe to use as your email and secure subscriptions comes under deep web. | Very much unsafe to use, the threat of cybercrime, and robbery. |
It is absolutely safe to surf around on the surface/clear web as there is no harm unless you are using a strong password and anti-theft devices for the better protection of your important data and computer system. Avoid using the areas where you have no or little knowledge. It is advised for your safety and security.
You may also like to read:

Author’s Bio: This article has been written by Rishika Desai, B.Tech Computer Engineering Student at Vishwakarma Institute of Information Technology (VIIT), Pune. She is a good dancer, poet and a writer. Animal love engulfs her heart and content writing comprises her present. You can follow Rishika on Twitter @ich_rish99.